What is post quantum cryptography?
When you break the world’s cyber secrets processes, you need to figure out how to keep secrets again.
Today’s world
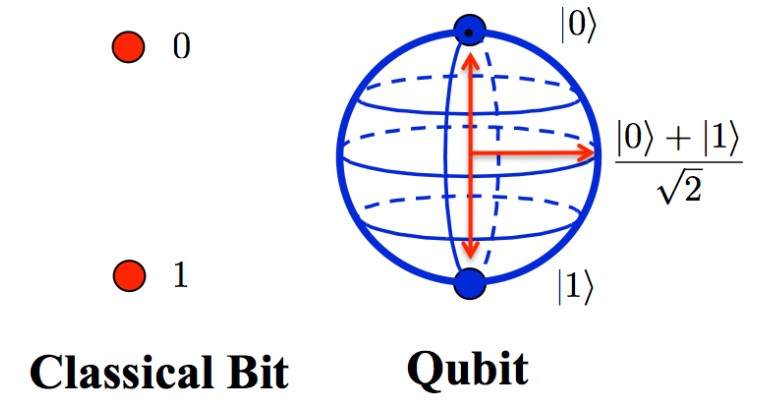
Most of us have heard of 1s and 0s as part of our understanding how computers speak and compute in binary; one of two positions, on or off. 1 or 0, bits. Binary is the smallest unit of data in computing.

Encryption uses the same processes and sends instructions to encrypt by using software to break down complex calculations to processes in binary and then return them back as the secured data. This continues in the processing logic of how we run symmetrical, and asymmetrical encryption today. Basically we set instructions for the computer to follow and in that we break down calculations in to binary states and send it to the processor to process. Each step is linear and the calculations today need to remember by the computer in every step that it takes in the path.
This is a simplified view, but we depend on these processes to be able to trust encryption and decryption in today’s world.
The Quantum Leap
Enter quantum computing where instead of 1s and 0s we use quantum states to produce qubits. A qubit operates in an undefined state, they can both be 0 and 1 at the same time, like being in two places at the same time. We can now tap into the power of individual atoms and molecules, additionally we’re now able to store, process and manipulate information simultaneously in ways that would have never be possible with “classical” computers.
Qubits can come in many forms including atoms, ions, photons and electrons. Unlike their binary cousins, qubits cannot be observed by looking directly at them, remember double slit theory? To measure qubits we have to use special techniques that by reference give us the position and result we’re looking for, this includes lasers to trap atoms and complex mathematical calculations.
Unlike the robustness of our bits and processors today, qubits are fragile. If a qubit accidentally interacts with its surroundings it can be distorted and cause errors, oh and it also needs to be kept at -273 degrees Celsius. Researchers must guard the molecule against two types of noise: shifts in the molecule’s orientation and changes in its angular momentum, and as you can image when dealing with something so small interference can come from a number of obstacles, radio, magnetic, electronic… etc.
As per IBM who are looking to house the largest quantum computer:
“Until now, we’ve relied on supercomputers to solve most problems. These are very large classical computers, often with thousands of classical CPU and GPU cores. However, supercomputers aren’t very good at solving certain types of problems, which seem easy at first glance. This is why we need quantum computers. Quantum computers can create vast multidimensional spaces in which to represent these very large problems. Classical supercomputers cannot do this.”
There is also an article from Autodesk that covers where we left off from Encryption in 1 Minute, highlighting what Alan Turing’s Turin machine would look like with qubit powers.
The problem:
While fragile, expensive and cutting edge, quantum computing has the ability to disrupt the existing encryption environment built over the last 30 year in a matter of seconds. Today, for example, it would take the Bitcoin network over 70,000,000,000,000,000,000,000,000 (70 septillion) years to crack a single AES-128 (bit) key. Currently, for 100 bits (slightly lower number), where it would take a normal computer 250 steps and an exorbitant amount of time, a quantum computer should only need about 50 steps and minutes or seconds, which means code-breaking would then be no more computationally demanding then processing todays algorithms.
As quantum computers build in size (# of qubits) the ease at which they will break today’s encryption requires a total rebuild of the way we keep secrets and the ability to maintain them.
You can imagine how impactful this will be against our use of modern day encryption, basically it would be able to break everything in an instant, like having a magical key to every single door lock in the world. We need to start thinking about how we’re going to maintain the secrets we don’t want everyone to know.
“The goal of post-quantum cryptography (also called quantum-resistant cryptography) is to develop cryptographic systems that are secure against both quantum and classical computers, and can interoperate with existing communications protocols and networks.
Some engineers even predict that within the next twenty or so years sufficiently large quantum computers will be built to break essentially all public key schemes currently in use. Historically, it has taken almost two decades to deploy our modern public key cryptography infrastructure. Therefore, regardless of whether we can estimate the exact time of the arrival of the quantum computing era, we must begin now to prepare our information security systems to be able to resist quantum computing.”
Hybrid:
“Quantum computers have the promise to outperform classical computers for certain tasks, but on currently available quantum hardware they can’t run long algorithms. They have too much noise as they interact with environment, which corrupts the information being processed,” said Marco Cerezo, a physicist specializing in quantum.
“With variational quantum algorithms, we get the best of both worlds. We can harness the power of quantum computers for tasks that classical computers can’t do easily, then use classical computers to compliment the computational power of quantum devices.”
While we wait for the future developments in qubit, materials and manufacturing we can leverage existing capabilities to do some of the “remedial” work. Allowing today’s tech to do what it does best, processing those 1s and 0s so that we can utilize quantum with the capabilities we have today. Google and more already have their strategies into the future:
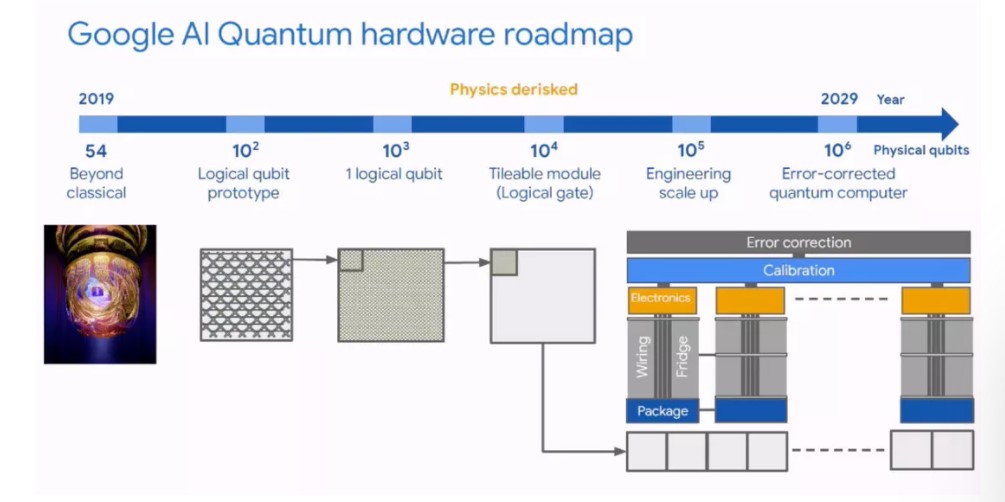
More can be found here at phys.org
This is the problem and the topic of the next ISC2 Belux chapter event with Phil Zimmermann as we dive in to the Post-Quantum Cryptography world. Please join us!
Fig A
bbc.co.uk
Fig B
autodesk.com
Fig C
Cnet.com

